Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
Impersonationis used to test changes in system configuration settings and in access rights. Impersonation is also used to demonstrate the implementation of automated processes in different roles.
| Tip |
|---|
Role required: impersonator. |
Two following parties are engaged in the Impersonation process:
Impersonator – can log in as another user temporarily.
Impersonated user – on behalf of whom the session is being performed.
If a user has the impersonator role, they can impersonate other users. If an administrator has an impersonator role, they can impersonate users and administrators. The impersonator has access to what the user can access in the system, including the same tools, UI layout, etc. The instance records impersonator's activities on behalf of the impersonated user, but specifies that it was within the impersonation session.
Impersonate a user
To impersonate a user, please complete the steps below:
In the banner, click on your user name or profile photo to open the user menu.
Select Impersonate. The Impersonate dialog box appears.
Start typing the name of the user you need to impersonate; once it appears in the selection field, select it.
You need to type at least two symbols.
To return to your original login session, please do the following steps:
Click on your user name or profile photo to open the user menu.
Click Back to me.
 Image Modified
Image Modified
| Info | |||||||||
|---|---|---|---|---|---|---|---|---|---|
|
...
|
...
|
Impersonation logs
...
Every time a user starts or stops impersonating another user, a related record appears in the Main Log (sys_log) storage. The format of the Message field in the record is:
| Panel | ||
|---|---|---|
| ||
Impersonation {start|end}: <impersonated_user> by: <impersonator> |
where both the impersonated user and impersonator are specified in the Display Name (username) format.
Both the Impersonation start and Impersonation end log records get created on behalf of the user whose identity will be used for further actions:
Impersonation startrecord: Impersonated userImpersonation endrecord: Impersonator
See the screenshot below for an example:
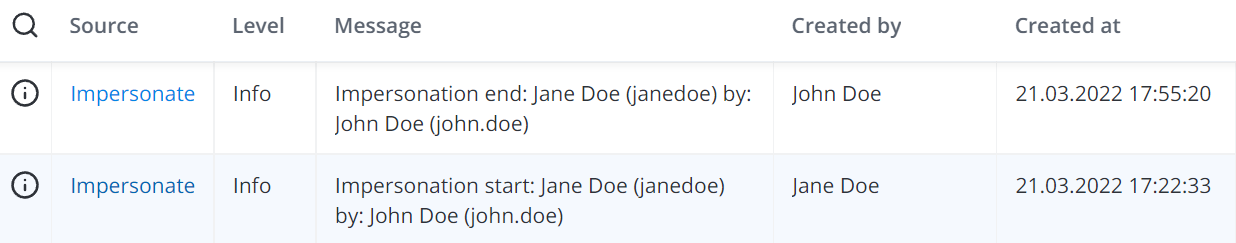 Image Added
Image Added
Actions of impersonated users are registered in System Logs
...
, like any other user activity.
...
Each log record resulting from an action of an impersonated user appears in the relevant log storage, as it would do without impersonation (refer to the Logging article for more details.):
Main Log (sys_log)
History (sys_history)
Script Log (sys_log_exception)
Exception Log (sys_log_script)
Record Deletion Log (sys_record_deletion_log)
A record logged for an impersonated user action can be recognized by the value of its Username field. In such a record, the impersonator's username in brackets follows the username of the impersonated user:
 Image Added
Image Added
| Table of Contents | ||||
|---|---|---|---|---|
|
...
