...
...
...
...
...
...
...
...
...
...
...
| Tip |
|---|
Before you begin Role required: impersonator |
...
...
...
...
| Info |
|---|
When you try to impersonate a user who is locked out or is inactive, the system generates a warning message and interrupts a process. To go on, you need to activate this user first. |
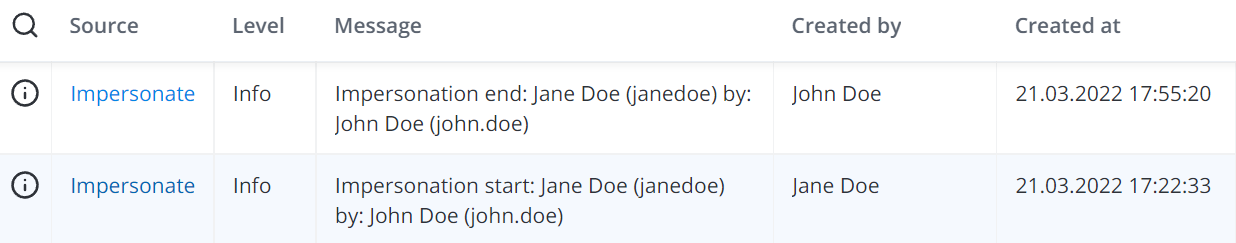
Impersonation logs
Impersonations are logged in the System History storage, like any other user activity. But the system point that the action was made within the impersonation session, so the impersonated user name will be specified in the Username column, and impersonator username will be specified near it in brackets like displayed on screenshot below.
...